How the Internet Really Works (For Hackers & Pentesters)
To become an effective ethical hacker or penetration tester, you must understand how the internet actually works beneath the surface.
What is Penetration Testing? Explained with Real Examples
Penetration testing (pentesting) is a core discipline in cybersecurity, designed to simulate real-world cyberattacks and identify security weaknesses before threat actors exploit them.
Top 10 Cybersecurity Myths Beginners Still Believe
Misconceptions in cybersecurity often mislead beginners and create unrealistic expectations about hacking and defense. This expert overview clarifies the most common myths to help you build a strong, accurate foundation in the field.
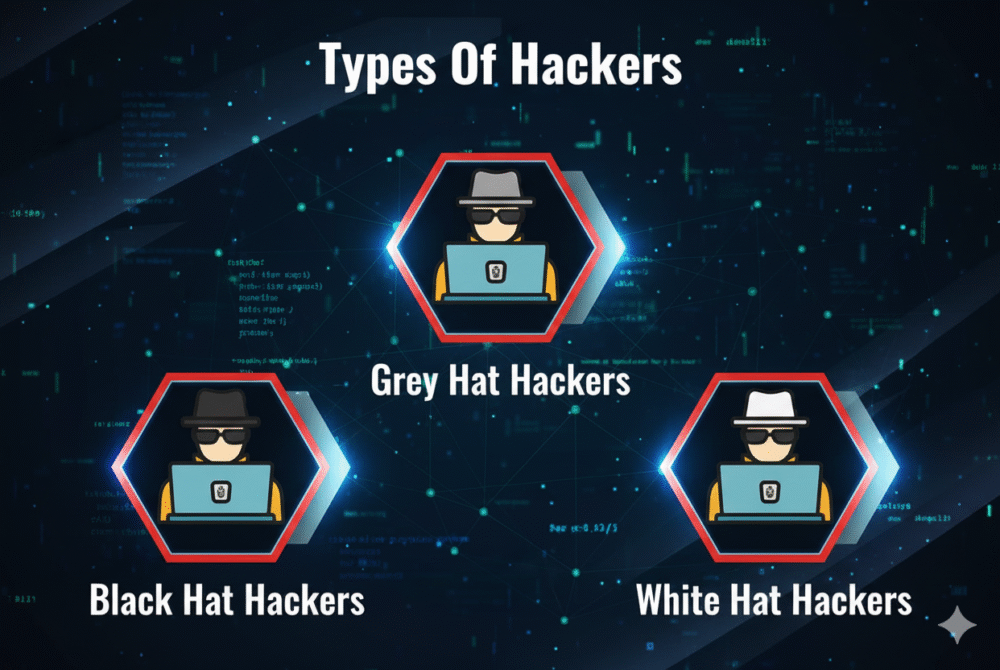
Types of Hackers: White Hat vs Black Hat vs Grey Hat
In the cybersecurity landscape, not all hackers operate with the same intentions, principles, or methodologies.
What is Ethical Hacking? A Complete Beginner’s Guide
Introduction Ethical hacking has become one of the most in-demand skills in today’s digital era. As cyberattacks grow more sophisticated, companies need professionals who can think like attackers to defend their systems. This is where ethical hackers, also known as white-hat hackers, come in. If you’re new to cybersecurity or thinking about starting a pentesting...