Introduction
The cybersecurity world is full of different types of hackers — each with different goals, ethics, and motivations. Understanding these hacker categories is essential for anyone starting their journey in ethical hacking, penetration testing, or cybersecurity in general.
In this article, we’ll break down the three main hacker types: White Hat, Black Hat, and Grey Hat. You’ll learn what each one does, how they operate, and why these classifications matter in the real world.
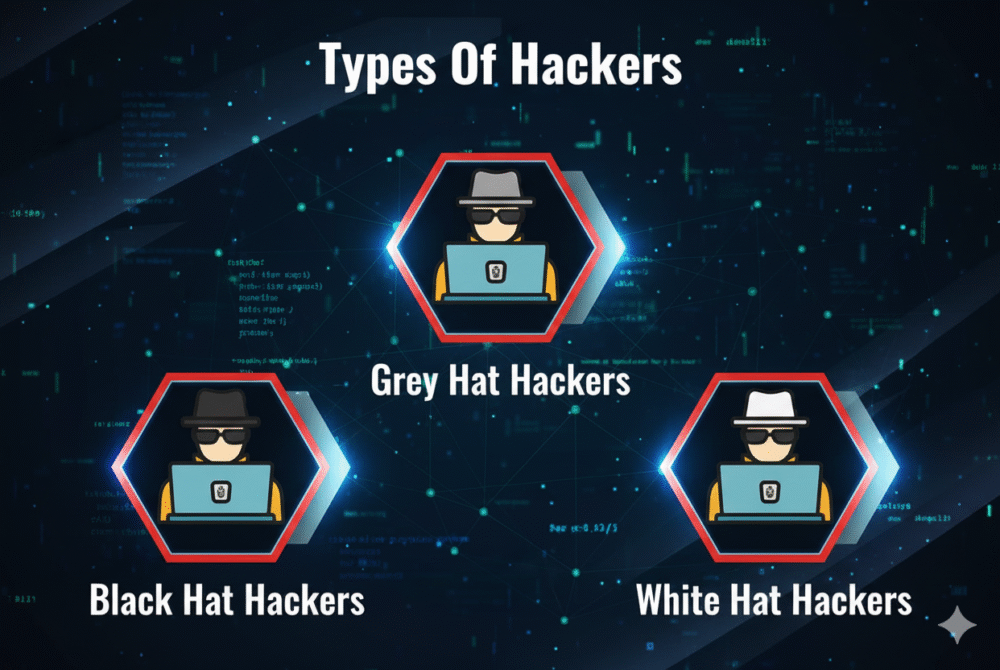
🛡️ 1. White Hat Hackers (Ethical Hackers)
White-hat hackers are cybersecurity professionals who legally test systems to help organizations strengthen security.
✔ What They Do
- Perform penetration tests
- Discover vulnerabilities and report them
- Improve security systems
- Help prevent data breaches
- Work for companies, governments, or cybersecurity firms
✔ Motivation
Protection, ethics, and improving cybersecurity.
✔ Tools They Use
- Kali Linux
- Nmap
- Burp Suite
- Metasploit
- Wireshark
These are the same tools used by attackers — but used ethically and with permission.
💀 2. Black Hat Hackers (Malicious Hackers)
Black-hat hackers are individuals who break into systems illegally for personal gain or malicious intent.
✔ What They Do
- Steal personal or financial data
- Install ransomware
- Sell stolen information on the dark web
- Break into systems without permission
- Cause system damage or disruption
✔ Motivation
Money, revenge, recognition, curiosity, or disruption.
✔ Common Targets
- Banks
- Companies
- Government systems
- Random users
- Weakly protected networks
Black-hat hacking is a criminal activity and punishable by law.
⚪ 3. Grey Hat Hackers (In Between)
Grey-hat hackers fall somewhere between ethical and malicious hackers.
✔ What They Do
- Hack without permission
- Do not intend to cause harm
- Sometimes report vulnerabilities to companies
- Sometimes ask for money in exchange for disclosure
✔ Motivation
Curiosity, challenge, or recognition — but without clear ethics.
✔ Why They’re Controversial
Although they rarely have malicious intentions, hacking without permission is still illegal.
🔍 Why Understanding Hacker Types Matters
Knowing the difference between these hacker categories helps you:
- Understand ethical boundaries
- Avoid illegal activities
- Choose the right cybersecurity career path
- Learn hacking skills safely and legally
- Understand attacker motivations
Ethical hacking requires permission, documentation, and professional conduct.
🧩 Real-World Example
Imagine a company with a vulnerable login page.
- A white-hat hacker finds the flaw during an authorized test and reports it.
- A black-hat hacker exploits it to steal data.
- A grey-hat hacker discovers it without permission and emails the company about it.
Same vulnerability.
Different ethics.
Different intentions.
🎯 Which Path Should You Choose?
If you’re learning cybersecurity with TechBlazes, your path is clear:
✅ Be a White Hat Hacker
- Legal
- Ethical
- High-paying career paths
- Opportunities in pentesting, SOC, bug bounty, and forensics
Ethical hacking is the foundation of professional cybersecurity.
⭐ Conclusion
White-hat, black-hat, and grey-hat hackers all use similar techniques, but their intentions and legal status set them apart.
As you grow in cybersecurity, always choose the ethical and legal path. Organizations around the world rely on ethical hackers to keep their systems safe — and there’s never been a better time to join the field.